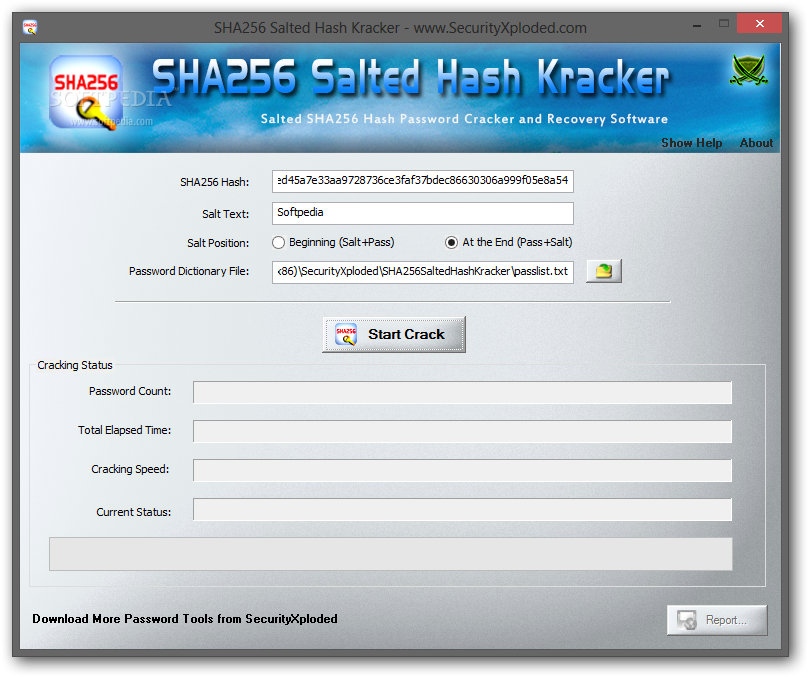
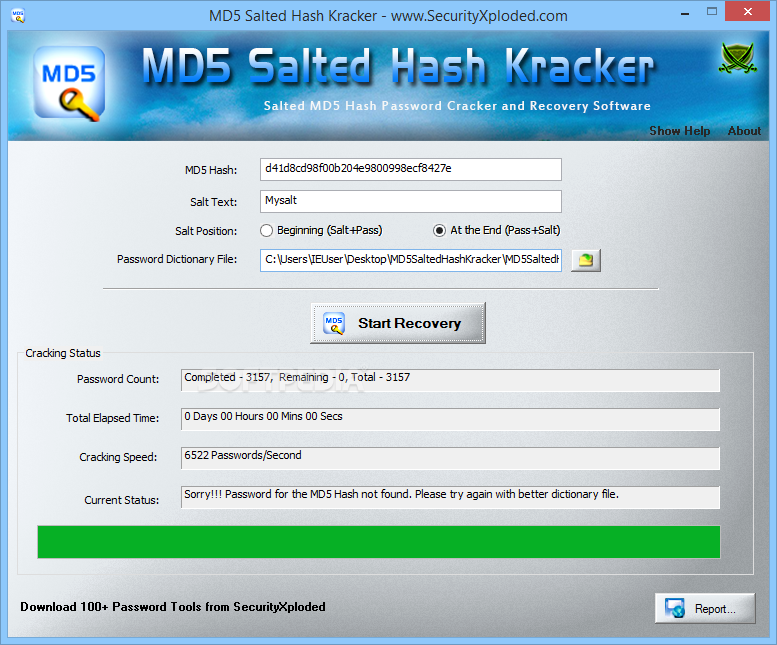
Decrypt Huawei router/firewall passwords. Huawei stores passwords using DES encryption when the crypted option is enabled. · GitHub
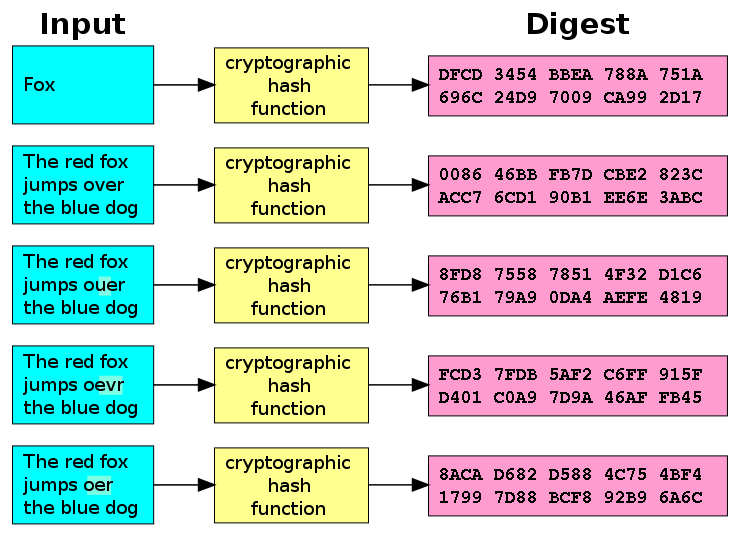
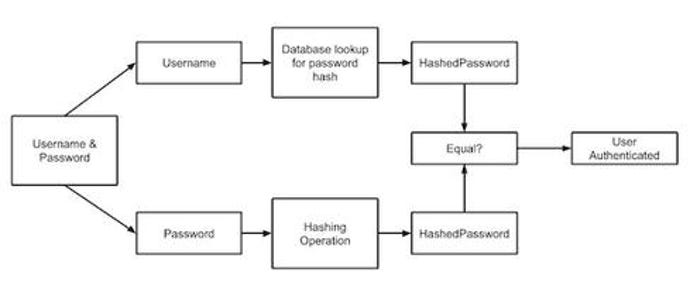
Password Hashes — How They Work, How They're Hacked, and How to Maximize Security | by Cassandra Corrales | Medium

Passwords and hacking: the jargon of hashing, salting and SHA-2 explained | Data and computer security | The Guardian